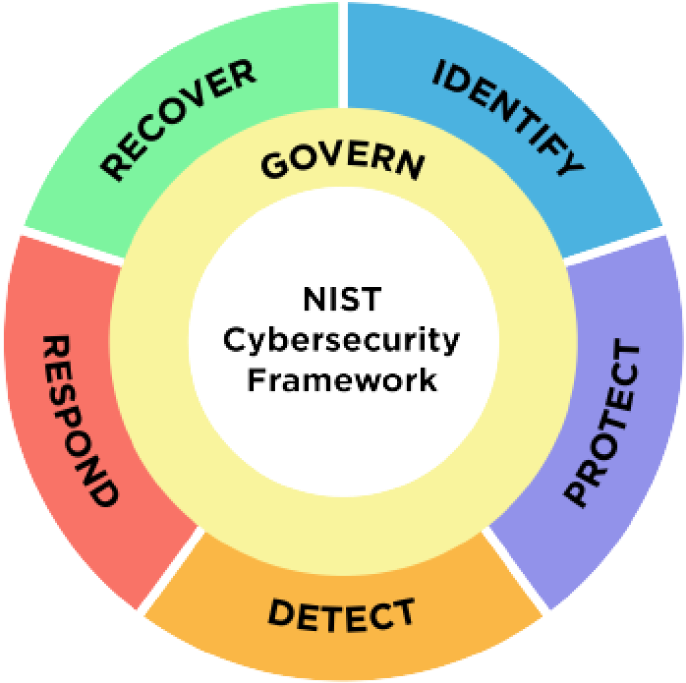
Welcome to Accrete's Trust Center. Our commitment to data privacy and security is embedded in every part of our business. Use Accrete's Trust Center to learn about our security posture and request access to our security documentation.
Risk Profile
Risk Profile
We have secure, reliable hosting that customers can depend on. We are happy to provide details about our risk mitigation practices and recovery objectives upon request.
Product Security
Product Security
We pay great attention to enterprise features such as access control and single sign on. We are happy to provide more details about our enterprise features upon request.
Reports
Reports
We may provide security-related reports upon request.
Self-Assessments
Self-Assessments
We are working on our security compliance. We can provide completed questionnaires upon request.
App Security
App Security
We take application security seriously and are putting together a program to monitor internal apps.
AI
AI
We take the usage of AI seriously in our organization and work to ensure security and reliability of the AI.
ESG
ESG
We prioritize and take environmental, social, and governance (ESG) considerations seriously in our operations and decision-making processes.
Data Privacy
Data Privacy
Privacy of customer data is top of mind. We follow industry best practices and follow all applicable privacy regulations.
Corporate Security
Corporate Security
We implement internal measures and practices to maintain a high standard of security.
Policies
Policies
We are currently working with experts to put together our company policies. Please contact us for more details.
Security Grades
Security Grades
We are constantly monitoring the security of our website. We will post our grades from public security rating agencies when they become available.
Risk Management
Risk Management
We have a dedicated team that manages security risks. We are happy to provide more details about our risk management practices upon request.
BC/DR
BC/DR
We have a business continuity plan in place to ensure that we can continue to operate in the event of a disaster.
Change Management
Change Management
We have a change and configuration management process in place to ensure that changes are properly reviewed and approved.